
From Lighthouse to Loran - Navigating GCP Security Auditing Tools
- Alex Morgan
- Cloud security
- March 1, 2024
Recently, I embarked on a journey into Google Cloud Platform (GCP), having spent a lot of time with AWS and Azure in the past, I wanted to dive into GCP and learn more. This exploration, fuelled by completing the Google Cybersecurity Certificate, and checking out sadcloud by NCCGroup , and the Enterprise Foundations Blueprint , led me to look more into auditing in GCP.
This blog post dives into the available auditing tools within GCP, focusing on both the standard tier offerings and open-source gems. But before we begin, let’s address some of the critical challenges we’ll be tackling:
- Gotta Keep ’em Separated - Access Control: Balancing identities, roles, scopes, exposed resources, open ports, and vulnerable functions can feel like guarding a medieval castle under siege. Oh, and serverless != threatless
- How many eggs ya got in those baskets? - Visibility: In security, we often preach, “Don’t put all your eggs in one basket.” But in the cloud, keeping track of “how many baskets” and “where all the eggs are” can be a real head-scratcher. Regular audits are our trusty magnifying glass in this game
- You left your keys in the door - Misconfiguration: Cloud environments are dynamic, and misconfigurations, whether at setup or during updates, can lurk in the shadows, creating headaches
Inspired by Scott Piper and his older post on auditing AWS accounts , I aim to follow a similar approach here for GCP. Scott, along with others has done great work when it comes to knowing how many baskets exist and where all the eggs are kept for AWS. The success of the tools and techniques proves that it is no easy job sometimes to keep track of those blasted eggs and baskets. Add an element of scale, and the challenge intensifies. So, let’s take a look at how GCP tackles this with built-in tools and explore open-source tools that can lend a hand.
Free Tools for Auditing GCP Security
Interestingly, I noticed that quite a few of the popular open-source tolls are now archived or end-of-life, such as Forseti and Netflix’s Security Monkey . The reason stated in Forseti for example is that over the years GCP Security has introduced features and capabilities that have addressed many of the areas and challenges these tools were targeting.
Built-in Google Tools
Security Command Center
https://cloud.google.com/security-command-center/docs/concepts-security-command-center-overview Launched in October 2022 (the first alpha was March 2021), Google Cloud Security Command Center (SCC) is a powerful tool which is included as part of the standard free tier for all GCP users. There are limitations compared to the tier which has both a pay-as-you-go or subscription model.


The standard tier includes functions like:
- Security Health Analytics: You’ll get alerts around misconfiguration, like open firewall ports, MFA not being enforced, public log bucket, public SQL, legacy authorisation enabled or outdated software. Focuses on high-severity.
- Web Security Scanner: Vuln checks in App Engine, Google Kubernetes Engine (GKE), and Compute Engine web applications. Custom scans are part of the standard tier, but managed scans are not. It’s worth checking out the best practises for this as there are some caveats, as ever, you need to be careful using this kind of tool in prod https://cloud.google.com/security-command-center/docs/concepts-web-security-scanner-overview#best_practices , web scanner does, as mentioned in the docs, err on the side of underreporting and doesn’t report on low-confidence findings.
- VPC Service Controls: Sets security boundaries and restricts data transfer within your VPC. https://cloud.google.com/vpc-service-controls/docs/enable , https://medium.com/google-cloud/mitigating-data-exfiltration-risks-in-gcp-using-vpc-service-controls-part-1-82e2b440197 .
- Anomaly Detection: This can check for leaked creds and cryptocurrency mining.
- Cloud Identity-Aware Proxy (IAP): Not a feature of Security Command Center, but worth highlighting. IAP Allows you to control access to apps with user identity and other contextual factors. Think Zero Trust over having an app open behind a VPN. This video shows an example: https://www.youtube.com/watch?v=ayTGOuCaxuc
- Cloud Asset Inventory: OK, so Cloud Asset Inventory is not part of Security Command Center, though Command Center does use the information and data from this to monitor for changes, suspicious activity and risks. Cloud Asset Inventory has a separate API and interface and can be used for discovery, inventory, and managing GCP resources.
Some of the limits of the standard tier to be aware of; you get a subset of the vulnerabilities and misconfigurations, fewer detection modules, limited customisation on reporting and analytics (like how far you can go back in reporting), fewer integrations with third party tools and the visibility is focused on project level, rather than organisation-wide. There is more info on the docs page which lists the features vs what is in the premium tier: https://cloud.google.com/security-command-center/docs/concepts-security-command-center-overview#tiers
GCP Scanner
https://github.com/google/gcp_scanner
Interestingly, this tool is in the Google GitHub repo but specifically states “This project is not an official Google project. It is not supported by Google and Google specifically disclaims all warranties as to its quality, merchantability, or fitness for a particular purpose.”.
Launched in March 2023, gcp_scanner can be used to evaluate the impact of VM/container compromise, GCP service account or OAtuh2 token key leakage. The tool does point out that Policy Analyzer (mentioned below) can help but “If you just have a GCP SA key, access to a previously compromised VM, or an OAUth2 refresh token, gcp_scanner is the best option to use.”
There is also a visualiser built into this tool too.

GCP Policy Analyser
https://cloud.google.com/policy-intelligence/docs/policy-analyzer-overview
Note
“After April 29, 2024, some Policy Intelligence features will only be available for customers with organization-level activations of the Premium tier of Security Command Center .”

One thing I like here is that there is a policy simulator: https://cloud.google.com/policy-intelligence/docs/iam-simulator-overview , so you can make adjustments and check to see what will happen. This was something customers of Duo used to ask us about a lot in Customer Success. This is the kind of feature that doesn’t often find an easy way off the backlog, so it’s nice to see here.
- Something else worth looking at might be the Change Risk Recommendation (https://cloud.google.com/recommender/docs/change-risk-recommendations) , which can flag risky changes or misconfigurations like deletion of projects, service accounts or changes to IAM policy. There are a bunch of recommenders for all sorts in GCP: https://cloud.google.com/recommender/docs/recommenders , a few security specific like the above and Cloud Run service recommenders and unattended project recommenders.
IAM Recommender
https://cloud.google.com/policy-intelligence/docs/role-recommendations-overview
Note
“After April 29, 2024, some Policy Intelligence features will only be available for customers with organization-level activations of the Premium tier of Security Command Center .”

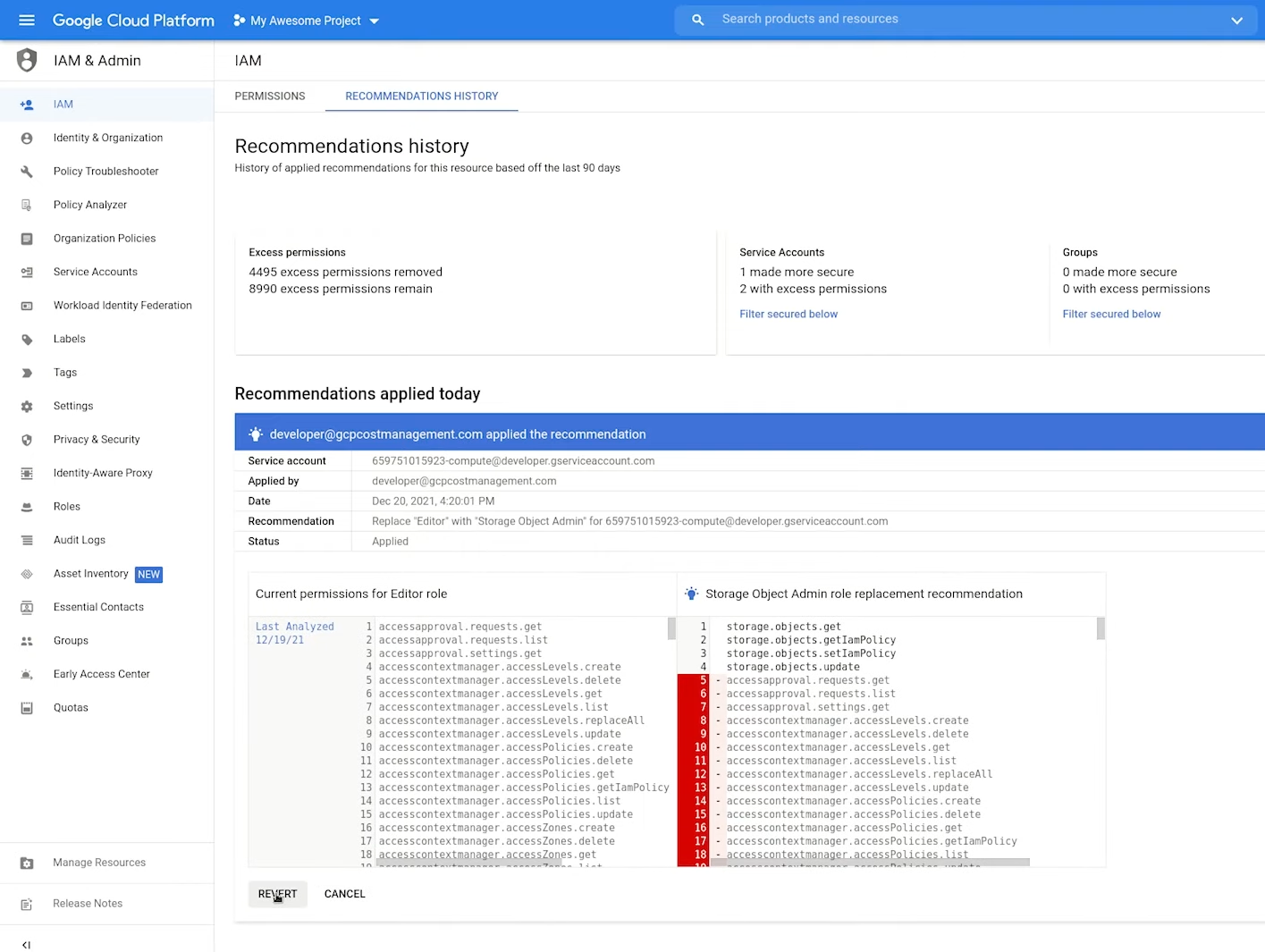
The recommender will analyse IAM policies and identify potential issues like overly permissive permissions. It’ll generate recommendations which you can apply directly or investigate further.
The history tab allows you to revert changes if you apply a change and something breaks.
CLI
This might seem an odd tool to point to but getting the most out of the exposed APIs sometimes means using the CLI. There are around 11,384 API methods within Google Cloud, so there is a lot to check out (https://gcp.permissions.cloud/ used as the data source).
Open-source Tools
Prowler

https://github.com/prowler-cloud/prowler
Prowler has come a long way since its release in September 2016. in-fact the Prowler team just got investment from Decibel VC https://prowler.com/blog/seed-funding/ . Prowler will output best practices assessments, audits, incident response, continuous monitoring, hardening and forensics readiness. It has a lot of in-built control coverage, so it’s able to check against these, such as: CIS, NIST 800, NIST CSF, CISA, RBI, FedRAMP, PCI-DSS, GDPR, HIPAA, FFIEC, SOC2, GXP, AWS Well-Architected Framework Security Pillar, AWS Foundational Technical Review (FTR), ENS (Spanish National Security Scheme) and custom security frameworks. You can also spit out reports to HTML, JSON, CVS.
ScoutSuite
https://github.com/nccgroup/ScoutSuite
Scout Suite was designed by security consultants/ auditors. It can quickly give you a report from an assessment, and these can be worked into automation. A multi-cloud tool, released in 2018. It has checks and functions for GCP, AWS and Azure. You can output reports to JSON and CSV, you can also get a nice HTML view.
 Here is the dashboard.
Here is the dashboard.
You can customise rules (https://github.com/nccgroup/ScoutSuite/wiki/Using-a-Custom-Ruleset ) and checks to align to your policies and needs.

Customisation can be as simple as flipping enabled to false or true, along with adjusting parameters.
There’s a nice post here for integrating ScoutSuite with Cloud Run: https://asrinandirin.medium.com/integrating-scoutsuite-with-cloud-run-serverless-security-and-compliance-automation-fbcef6141bb9
CloudSploit
https://github.com/aquasecurity/cloudsploit

Designed to allow detection of security risks in cloud infrastructure accounts. These scripts are designed to return a series of potential misconfigurations and security risks.
GCP configuration instructions: https://github.com/aquasecurity/cloudsploit/blob/master/docs/gcp.md#cloud-provider-configuration
Cloud Custodian
https://cloudcustodian.io/ - https://github.com/cloud-custodian/cloud-custodian

Arriving in 2016, Cloud Custodian is more of an enforcement rules engine. It can take action on its findings, such as powering down instances and changing the visibility of buckets to private. A good portion of this is focused on cost management the idea is that this will run on a schedule to enforce your policies. I’ve briefly looked at Cloud Custodian, so there is more to check out, though it seems light on rule examples, and the enforcing and terminating resources function means it’ll require a good amount of caution and planning to use.
https://cloudcustodian.io/docs/gcp/gettingstarted.html
Other mentions
- Steampipe: https://github.com/turbot/steampipe - I mentioned the Google Cloud CLI above, and it’s worth also pointing to Steampipe here. You can instantly query APIs using SQL, across cloud providers and other sources. They have a GCP plugin. The benefit to Steampipe is that you can join with other cloud sources to give you an open-source dashboard to query. A couple of blog posts you may want to check out here: https://medium.com/@ravishtiwari/steampipe-monitoring-multi-cloud-infra-with-plugins-and-mods-c3f8c84bc7bc - https://briansuk.medium.com/connecting-steampipe-with-google-bigquery-ae37f258090f
- Purple Panda: https://github.com/carlospolop/PurplePanda - Designed from the pentest perspective but a good tool for blue teams also, it can help identify privilege escalation paths and risky permissions. GCP discovery: https://github.com/carlospolop/PurplePanda/tree/master/intel/google
- HackTricks Pentesting Details: https://cloud.hacktricks.xyz/pentesting-cloud/gcp-security - Not a tool really but if you’re interested in the possible exploits and paths this is a great resource to check out (also plenty more in here)
- Cloud Vuln DB: https://www.cloudvulndb.org/ - A centralised cloud vulnerability database, which is a great thing for the industry. Includes remediation steps and covers across GCP, AWS and Azure. Built off of Scott Piper’s Cloud Service Security Provider Security Mistakes . This site is sponsored by Wiz , which is a product that I’ve only heard good things about and although falls outside of this post may well worth taking a look at.
- Chronicle: https://cloud.google.com/chronicle - Google’s SIEM/SOAR. A separate product from Security Command Center. I recently got to play around with Chronicle in some labs and was quite impressed and from what I’ve heard folks have said that over the past year, Chronicle has come on leaps and bounds.
- GCPBucketBrute: https://github.com/RhinoSecurityLabs/GCPBucketBrute - A script to enumerate Google Storage buckets, determine what access you have to them, and determine if they can be privilege escalated
- Awesome Cloud Security: https://github.com/4ndersonLin/awesome-cloud-security - As ever the awesome lists have a whole bunch of stuff in there to check out
Conclusion
There are plenty more tools out there, and new ones emerging all the time. I haven’t covered them all here, hopefully, this breakdown shows the progress that GCP has made on building security in as well as the tools like Prowler that are growing and expanding. Remember, the best toolset for you depends on your specific needs. Consider factors like the complexity of your environment, your security priorities, and your team’s technical expertise.
Google Cloud Platform has some great tools built-in already, which some of the open-source tools have given way to. Prowler and ScoutSuite are tools that can give a good lay of the land with actions to take, and things like Steampipe can help with visibility across GCP and further.



